Infrastructure business
While considering even latent risks,
we offer infrastructure services that secure
the continuity of each client’s business.
We provide ICT infrastructure that secures the continuity of each client’s business. This is an important mission of K’s. We solve clients’ problems about ICT infrastructure with comprehensive services, including the design, establishment, and maintenance of networks, desktop virtualization, cloud services, and security measures. In addition, we respond to and solve trouble in day-to-day operation, and support stable operation.
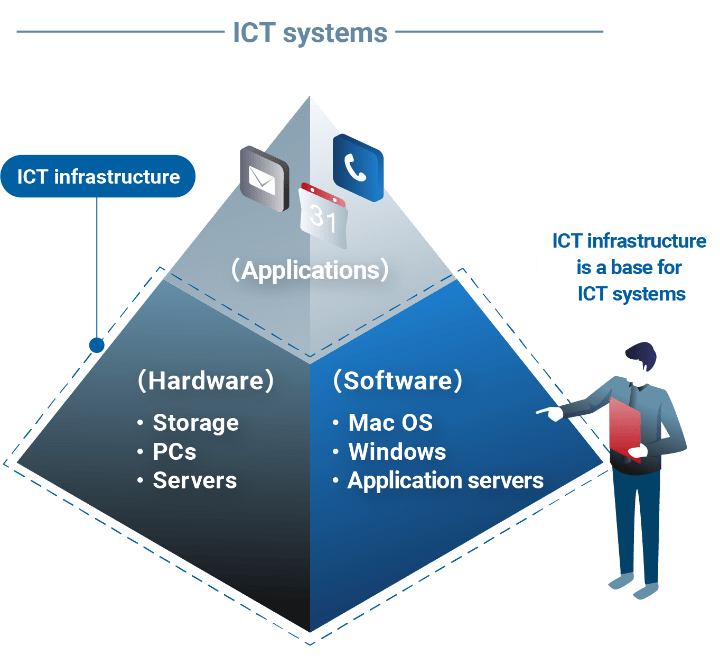
ICT infrastructure supports ICT systems.
ICT infrastructure means equipment and facilities for operating ICT systems as it is named. If ICT infrastructure is insufficient, there is a risk of security trouble, such as a virus attack, leakage of confidential information, and data falsification. In addition, it may cause the failure or malfunction of hardware.
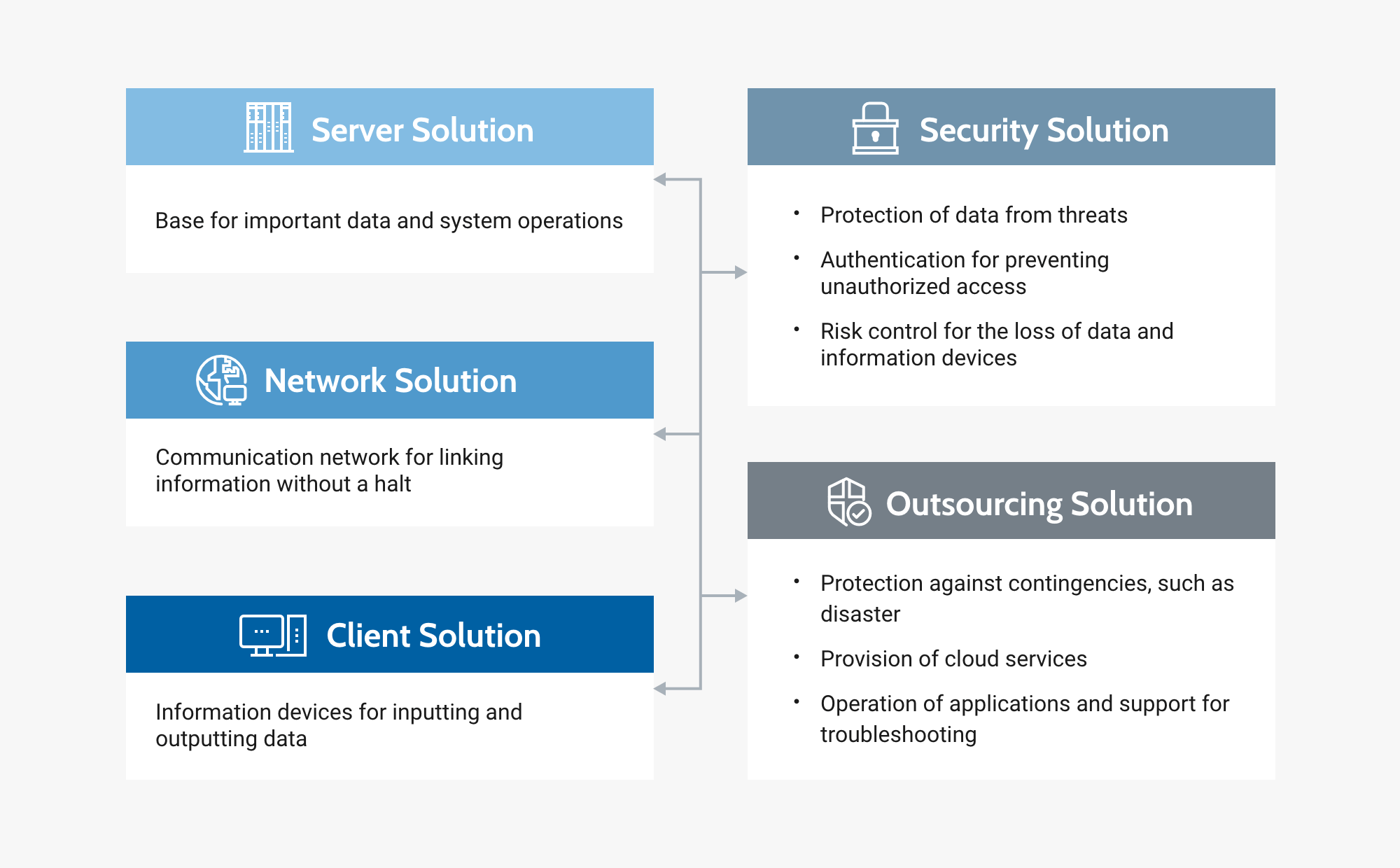
Conceptual diagram of ICT infrastructure business
Strengths of K’s
STRENGTH_01Provision of consistent services, including proposal, installation, and follow-up after installation
We offer consistent services, including consultation for issues, proposal for solutions, installation of infrastructure, system development, and follow-up after installation regarding operation and trouble. We grasp the usage environment, identify the causes of trouble and contingencies, and propose solutions, to support clients so that their business operations will not be hindered. In addition, we select hardware and software flexibly when requested.

STRENGTH_02Planning and provision of cloud services for the ICT infrastructure environment
We are also able to plan and provide ICT infrastructure solutions, including operation and support, as cloud services. By outsourcing the development of an ICT infrastructure environment, clients can reduce the augmenting burdens of management and operation.

List of services
Virtual desktop service
Since it is now common to use PCs for business, it is necessary to develop an environment for dealing with trouble regarding data handling and allowing diverse workstyles. The use of data-less PCs is the most effective method for coping with the risk of loss of business data and loss of data taken out of offices for business or telecommuting. Administrators and users can use such PCs safely without stress.
Multifactor authentication service
The frequency of authentication is increasing rapidly, due to rapidly spreading cloud services and the diversification of workstyles fueled by measures against COVID-19. Under the assumption that it is difficult to record all log-in information for each service, we solve operation problems with multifactor authentication based on “ownership information” and “biological information” without relying on “memory information” such as passwords.
Wireless LAN environment survey service
Through the distribution of tablets and IoT devices, the demand for wireless networks is growing in all kinds of fields. To cope with trouble, such as “It’s too slow” and “It cannot be connected,” we visualize the radio wave condition, which cannot be grasped through an environmental survey, by using a dedicated tool, measure radio field intensity, interference wave, and communication speed, and realize a stable wireless network environment.
Maintenance service
Experienced engineers will support the maintenance of hardware and deal with software trouble. We support clients in identifying and dealing with trouble in their day-to-day operations on site or remotely. We make efforts to become the closest, reliable one for clients.
Issues that can be resolved
Clients’ issues vary according to business operations and workstyles. K’s puts importance on the dialogue with each client, and first asks about the hardware and software in each client’s ICT environment, issues with networks, and security policies. Based on the dialogue, we propose solutions that would not augment the burden of administration.
- Measures against the leakage of information
- Simplification of password management
- Acceleration of communication speed
- Asset management
- Support for telecommuting
- Improvement in communication
- Shortening of troubleshooting time
